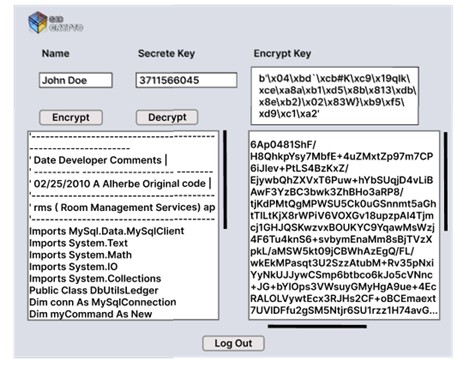
Gid Crypto: Application for End-to-End Encrypt and Decrypt E-mail and Data
Main Article Content
Abstract
Privacy and security in our digital environment have become essential today. Some data stored on hard disks, in flash memory, or exchanged through our communication channels is sensitive and should be kept confidential. Additionally, documents containing confidential information, such as business algorithms or new application coding, require adequate measures to ensure privacy and security. Therefore, data encryption is crucial in protecting information from being intercepted, misused, or stolen. While encryption tools are available for business e-mails, using these tools often requires subscribing as a member and paying extra fees. Effective tools are not limited to e-mail alone. Still, they can also be applied to any text data that requires a high level of security and complexity to ensure the protection of the data for a duration longer than it needs to be safeguarded. Our research aims to develop a stand-alone application that encrypts data to ensure its confidentiality without additional subscriptions or fees. The application is designed to be user-friendly, with fast encryption and decryption capabilities. It can be used not only for encrypting and decrypting e-mail messages but also for programming languages and Excel data. The application development utilizes techniques such as Diffe-Hellman, Mersenne Twister, and AES, arranged in layers to generate complex ciphertext that is difficult to decrypt without the developed application. LabVIEW was used for testing encryption speed. The attempt to attack encrypted data was subjected, but the result yielded no successful key retrieval.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
cloudHQ. (2021, April 6). 50 Years of E-mail. CISSION. https://www.prnewswire.com/news-releases/50-years-of-email-301262676.html
Radicaati Team (2021, February 22). E-mail Statistics Report, 2021-2025. Statista Radicati, https://www.radicati.com/?p=17209
Ghali, C.; Stubblefield, A.; Knapp, E.; Li, J.; Schmidt, B.; Boeuf, J. (2017, December 27), Application Layer Transport Security, Google Cloud whitepaper. https://cloud.google.com/docs/security/encryption-in-transit/application-layer-transport-security
Nohe, P. (2018, October 15), Apple, Microsoft, Google Announce Plans to Disable TLS 1.0, TLS 1.1. hashedout. https://www.thesslstore.com/blog/apple-microsoft-google-disable-tls-1-0-tls-1-1/
Just, M. Diffie-Hellman Key Agreement. In Van Tilborg H.C.A. (Eds.), Encyclopedia of Cryptography and Security (pp. 154-163). Springer. 2005. https://www.academia.edu/63723313/Springer_Encyclopedia_of_Cryptography_and_Security
Jagannatam, A. (2008), Mersenne Twister – A Pseudo Random Number Generator and its Variants. [Technical report, Department of Electrical Computer Engineering, George Mason University].
Kak, A. Lecture 8: AES: The Advanced Encryption Standard, Lecture Notes on Computer and Network Security, Purdue University. 2020. https://engineering.purdue.edu/kak/compsec/NewLectures/Lecture8.pdf
O S. N.; Vankamanidi S. N. Comparative Analysis of MOD-ECDH Algorithm and Various Algorithms. Journal of Industrial Engineering & Production Research. 2020, 31(2), 302-308. https://do.org/10.22068/ijiepr.31.2.301
Hamid N.; Nikil D.; Sandip R.; Francesco R.; Indranil B.; Rosario C. Post-quantum Lattice-based Cryptography Implementations: A Survey. ACM Computing Surveys. 2019, 51(6), 1-41. https://doi.org/10.1145/3292548
Tain, X.; Benkrid, K. (2009, July 29 – August 1). Mersenne Twister random number generation on FPGA, CPU and GPU NASA/ESA [Conference session]. 2009 Conference on Adaptive Hardware and System, San Franciso, CA, United States. https://ieeexplore.ieee.org/document/5325420
Vigna, S. (2019, November 14). Is it high time we let go of the Mersenne Twister. Arxiv. https://arxiv.org/pdf/1910.06437.pdf
Rimkienė, R. (2022, August 29), What is AES encryption and how does it work?. Cybernews, https://cybernews.com/resources/what-is-aes-encryption/
Schwenk, J. Guide to Internet Cryptography: Security Protocols and Real-World Attack Implications. Springer. 2022. https://link.springer.com/book/10.1007/978-3-031-19439-9
Kiltz, E., O’Neill A.; Smith, A. Instantiablity of RSA_OAEP Under Chosen-Plaintext Attacj. Journal of Cryptology. 2017, 30(1), 889-919. https://doi.org/10.1007/s00145-016-9238-4
Huang, Z.; Liu, S.; Qin, B. Sender Equivocable Encryption Schemes Secure against Chosen-Ciphertext Attacks Revisited. Journal of Applied Mathematics and Computer Science. 2015. 25(2), 369-389. https://doi.org/10.1007/978-3-642-36362-7_23
Latif, I. H. (2021, August 14). Time Evaluation Of Different Cryptography Algorithms Using Labview [Confernce session]. The 4th Postgraduate Engineering Conference in Materials Science and Engineering, Baghdad, Iraq. https://iopscience.iop.org/article/10.1088/1757-899X/745/1/012039
Microsoft (2023, July 31). Preparing for TLS 1.2 in Office 355 and Office 365 GCC. Microsoft, https://docs.microsoft.com/en-us/microsoft-365/compliance/prepare-tls-1.2-in-office-365?view=o365-worldwide
egress (2021, January 17). How to encrypt Outlook e-mails in transit. egress. https://www.egress.com/blog/email-encryption/encrypt-outlook-emails-in-transit
Microsoft 365 (2023, August 8), E-mail encryption. Microsoft, https://docs.microsoft.com/en-us/microsoft-365/compliance/email-encryption?view=o365-worldwide
Posteo (2021, December 12). POSTEO: E-mail, calendar, address, book, notes. POSTEO. https://posteo.de/en
Tutanota (2022, March 25). Tutanota Secure e-mail for everybody. Tutanota. https://tutanota.com/
Lalabit (2022, June 10). Secure e-mail for the world. Lavabit. 2022. https://lavabit.com/
Trustifi, (2022, October 7). Trustifi E-mail Security that is Easy to Deploy, Manage, and Use. Trustifi. https://trustifi.com/
Preveil, (2022, August 19). Preveil Simple Secure Compliment. Preveil. https://www.preveil.com/
Signal, (2022, Febuary 26). Speak Freely. Signal. https://signal.org/en/
Livington, J. D.; Kirubakarn, E.; Johnraja, J. I (2021, August 4). Implementing Client-Side Encryption for Enforcing Data Privacy on the Web Using Symmetric Cryptography: A Research Paper [Conference session]. Third International Conference on Information Management and Machine Intelligence, Singapore. https://link.springer.com/chapter/10.1007/978-981-19-2065-3_2
Moon, M. E.; Colonel, M. E. How America Lost its Secrets: Edward Snowden, The Man and The Thief By Edward Jay Epstein New York, N.Y.; Alfred A. Knopf. Journal of Strategic Security. 2017, 10(1), 143-147. https://www.jstor.org/stable/26466898