การประยุกต์ใช้เทคนิคการเรียนรู้ของเครื่องในการตรวจจับการบุกรุกเครือข่าย: การศึกษาเชิงประจักษ์โดยใช้ชุดข้อมูล UNSW-NB15
Main Article Content
บทคัดย่อ
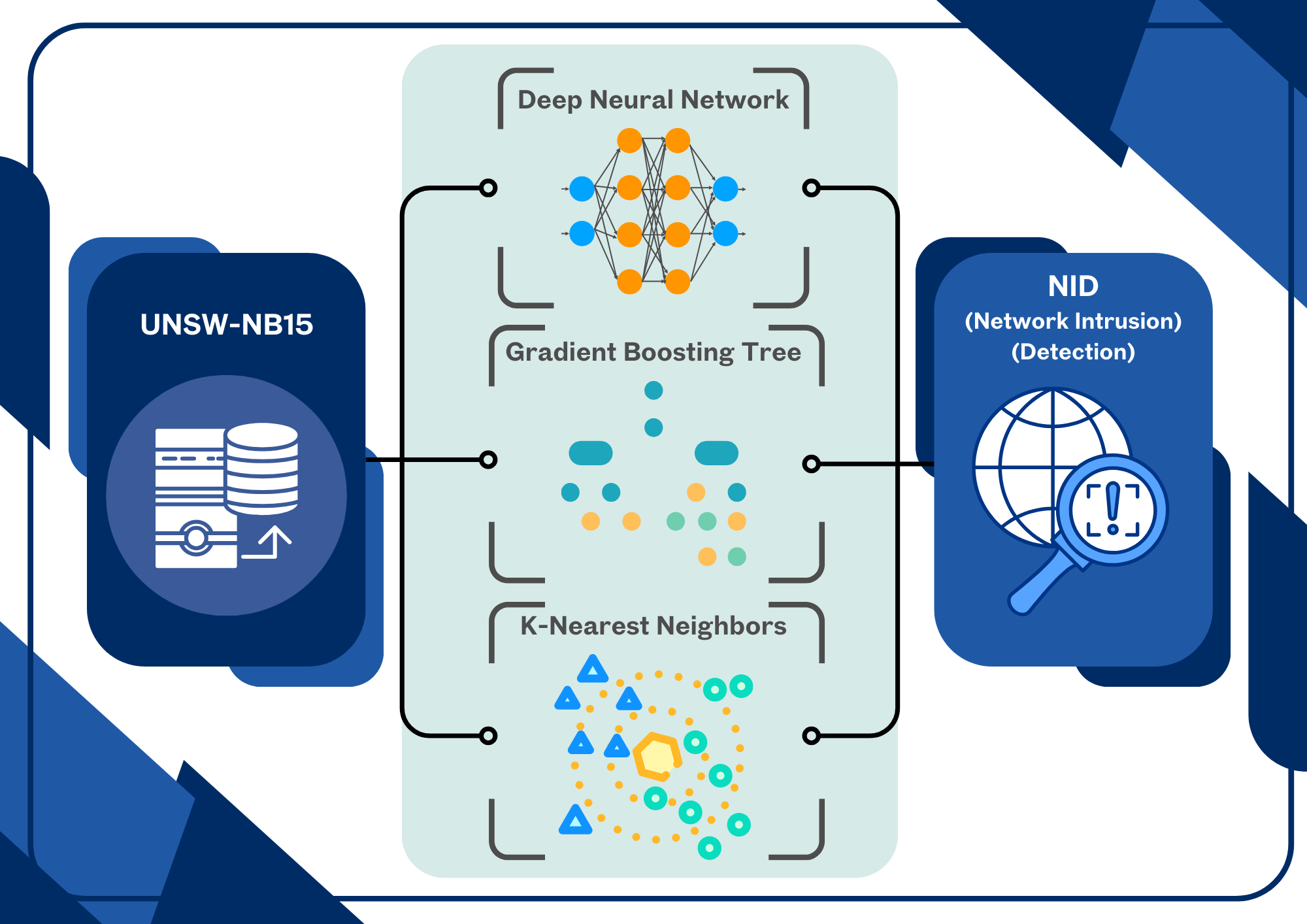
งานวิจัยนี้มีวัตถุประสงค์เพื่อเปรียบเทียบประสิทธิภาพของอัลกอริทึมในการเรียนรู้ของเครื่อง โดยการศึกษาและทดสอบอัลกอริทึมต่าง ๆ ได้แก่ Deep Neural Network (DNN) Gradient Boost Tree (GBT) และ k-nearest Neighbor (KNN) กับชุดข้อมูล UNSW-NB15 โดยมีจำนวนข้อมูล 2,540,047 บันทึกข้อมูล และมีจำนวนฟีเจอร์ต่าง ๆ ทั้งสิ้น 49 ฟีเจอร์ที่สำคัญ และประเภทการโจมตีทั้งหมด 9 ประเภท ด้วยการ Split Test ใช้ชุดข้อมูลสำหรับการฝึก Training Data (ร้อยละ 80) และทดสอบ Test Data (ร้อยละ 20) โดยการเขียนโปรแกรมด้วยภาษา Python และการใช้ Library ที่เหมาะสมสำหรับอัลกอริทึมต่าง ๆ ในการทดลองและประมวลผลผลลัพธ์ หลังจากวิจัยและปรับปรุงคุณลักษณะของข้อมูลในทุก 3 เทคนิคที่กล่าวมา ผลการทดลองพบว่า Deep Neural Network (DNN) มีความถูกต้องสูงที่สุดที่ร้อยละ 87.3% Gradient Boost Tree (GBT) ได้ค่าความถูกต้องสูงที่สุดที่ร้อยละ 99.1% และ k-nearest Neighbor (KNN) ได้ค่าความถูกต้อง 99% ผลการวิจัยนี้ช่วยให้เข้าใจถึงประสิทธิภาพของอัลกอริทึมต่าง ๆ ในการเรียนรู้ของเครื่องและสามารถเลือกใช้อัลกอริทึมที่เหมาะสมสำหรับงานและการศึกษาต่าง ๆ ในอนาคต
Article Details

อนุญาตภายใต้เงื่อนไข Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
เอกสารอ้างอิง
Avital, M.; Bittencourt, L. F.; Santos, J. L.; Marín, D. B.; Rojas, L. C. Global DDoS Threat Landscape Report 2019.
Axelsson, S. The Base-Rate Fallacy and the Difficulty of Intrusion Detection. ACM Trans. Inf. Syst. Secur. 2000, 3(3), 186-205. https://doi.org/10.1145/357830.357849
Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A. A. A Detailed Analysis of the KDD CUP 99 Data Set. Proc. 2009 IEEE Symp. Comput. Intell. Secur. Def. Appl., 2009, 1-6. https://doi.org/10.1109/CISDA.2009.5356528
Creech, G.; Hu, J.; Williams, R. A Survey and Comparison of Distributed Intrusion Detection System. J. Netw. Comput. Appl. 2014, 40, 12-33.
Nassar, M.; Alazab, M.; Venkatraman, S. Anomaly Intrusion Detection System: A Comprehensive Review. IEEE Access 2019, 7, 166152-166188.
Garcia, S.; Grill, M.; Stiborek, J.; Zunino, A. An Empirical Comparison of Botnet Detection Methods. Comput. Secur. 2014, 45, 100-123. https://doi.org/10.1016/j.cose.2014.05.011
Moustafa, N.; Slay, J. UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems (UNSW-NB15 Network Data Set). In Proceedings of the Military Communications and Information Systems Conference (MilCIS), 2015; IEEE: 2015. https://doi.org/10.1109/MilCIS.2015.7348942
Singh, M.; Kaur, M.; Singh, S. Intrusion Detection System Using Deep Learning Techniques: A Review. 2019.
Yang, X.; Wu, M.; Wei, W.; Li, L. A Boosted Trees Algorithm for Network Intrusion Detection. 2019.
Zhang, Z.; Luo, L.; Zhang, L.; Zhang, Y. Network Intrusion Detection System Based on k-Nearest Neighbor Algorithm. 2019.
Tukey, J. W. Exploratory Data Analysis; 1977.
Ashok, K.; Kumar, S.; Kumari, A.; Saini, A. Edge Computing Based IDS Detecting Threats Using Machine Learning and PyCaret. 2023, DOI: 10.1109/CISES58720.2023.10183591. https://doi.org/10.1109/CISES58720.2023.10183591
Mitchell, T. M. Machine Learning; McGraw Hill: 1997.
Hastie, T.; Tibshirani, R.; Friedman, J. The Elements of Statistical Learning: Data Mining, Inference, and Prediction; Springer Science & Business Media: 2009. https://doi.org/10.1007/978-0-387-84858-7
Goodfellow, I.; Bengio, Y.; Courville, A. Deep Learning; MIT Press: 2016.
Krizhevsky, A.; Sutskever, I.; Hinton, G. E. ImageNet Classification with Deep Convolutional Neural Networks. In Advances in Neural Information Processing Systems, 2012; pp 1097-1105.
LeCun, Y.; Bengio, Y.; Hinton, G. Deep Learning. Nature 2015, 521(7553), 436-444. https://doi.org/10.1038/nature14539
Krizhevsky, A.; Sutskever, I.; Hinton, G. E. ImageNet Classification with Deep Convolutional Neural Networks. In Advances in Neural Information Processing Systems, 2012; pp 1097-1105.
LeCun, Y.; Bengio, Y.; Hinton, G. Deep Learning. Nature 2015, 521 (7553), 436-444. https://doi.org/10.1038/nature14539
Duangklang, P.; Kruakaew, R. Models for Automatic Aircraft Type Prediction. NKRAFA J. Sci. Technol. 2019.
Confusion Matrix - An Overview. Available online: https://www.sciencedirect.com/topics/engineering/ confusion-matrix (accessed on June 8, 2022).
Using Machine Learning Techniques Random Forest and Neural Network to Detect Cyber Attacks. 2023, DOI: 10.14293/pr2199.000059.v1. https://doi.org/10.14293/PR2199.000059.v1
Patrick, S. Machine Learning Based Network Attacks Classification. 2023, DOI: 10.1109/icpeca56706. 2023.10075818.
Jingwen, W.; Peilong, L. MalIoT: Scalable and Real-time Malware Traffic Detection for IoT Networks. 2023, arXiv:2304.00623.
Michael, G. A Machine-Learning Procedure to Detect Network Attacks. J. Complex Netw. 2023, DOI: 10.1093/comnet/cnad017. https://doi.org/10.1093/comnet/cnad017
Ashok, K.; Kumar, S.; Kumari, A.; Saini, A. Edge Computing Based IDS Detecting Threats Using Machine Learning and PyCaret. 2023, DOI: 10.1109/CISES58720.2023.10183591. https://doi.org/10.1109/CISES58720.2023.10183591
Fuat, T. Analysis of Intrusion Detection Systems in UNSW-NB15 and NSL-KDD Datasets with Machine Learning Algorithms. Bitlis Eren Üniversitesi Fen Bilimleri Dergisi 2023, DOI: 10.17798/bitlisfen.1240469. https://doi.org/10.17798/bitlisfen.1240469
Aleesa, A.; Thanoun, M.; Mohammed, A.; Sahar, N. DEEP-INTRUSION DETECTION SYSTEM WITH ENHANCED UNSW-NB15 DATASET BASED ON DEEP LEARNING TECHNIQUES. J. Eng. Sci. Technol. 2021, 16, 711-727.
Zhou, Y.; Han, M.; Liu, L.; He, J.S.; Wang, Y. Deep Learning Approach for Cyberattack Detection. In IEEE INFOCOM 2018-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS); IEEE: 2018, pp 262-267. https://doi.org/10.1109/INFCOMW.2018.8407032
Faker, O.; Dogdu, E. Intrusion Detection Using Big Data and Deep Learning Techniques. ACM: 2019, DOI: 10.1145/3299815.3314439. https://doi.org/10.1145/3299815.3314439
Kasongo, S. M.; Sun, Y. Performance Analysis of Intrusion Detection Systems Using a Feature Selection Method on the UNSW-NB15 Dataset. J. Big Data 2020, 7, 105, DOI: 10.1186/s40537-020-00379-6. https://doi.org/10.1186/s40537-020-00379-6
Rahman, O.; Quraishi, M. A. G. Experimental Analysis of Random Forest, K-Nearest Neighbor and Support Vector Machine Anomaly Detection. 2019, DOI: 10.13140/RG.2.2.19998.18245. [33]McKinney, W. Pandas, Python Data Analysis Library. 2015.
Oliphant, T. E. Guide to Numpy; Trelgol Publishing: 2006, 1, 85.
Khandare, A.; Agarwal, N.; Bodhankar, A.; Kulkarni, A.; Mane, I. Analysis of Python Libraries for Artificial Intelligence. In Intelligent Computing and Networking: Proceedings of IC-ICN 2022; Springer Nature Singapore: Singapore, 2023, pp 157-177. https://doi.org/10.1007/978-981-99-0071-8_13
Ari, N.; Ustazhanov, M. Matplotlib in Python. In 2014 11th International Conference on Electronics, Computer and Computation (ICECCO); IEEE: 2014, pp 1-6. https://doi.org/10.1109/ICECCO.2014.6997585
Sundaram, J.; Gowri, K.; Devaraju, S.; Gokuldev, S.; Jayaprakash, S.; Anandaram, H.; Thenmozhi, M. An Exploration of Python Libraries in Machine Learning Models for Data Science. In Advanced Interdisciplinary Applications of Machine Learning Python Libraries for Data Science; IGI Global: 2023, pp 1-31. https://doi.org/10.4018/978-1-6684-8696-2.ch001